Linux SSH Security Best Practices to secure your Cloud Servers
SSH (Secure shell) is a cryptographic network protocol used to connect to a remote server securely and transfer data in encrypted form between the host and the client. SSH allows data encryption in a way that attackers cannot access your details such as user information and passwords.
However, at times, it can happen that a server can get compromised or attacked due to improper security practices implemented for the SSH server. This article outlines some of the steps in which the SSH server can be secured in Linux Cloud Servers.
For the entirety of this article, once any values are changed/set in the SSHD configuration file ( /etc/ssh/sshd_config ), it is required that the SSHD service be restarted with the help of below commands:
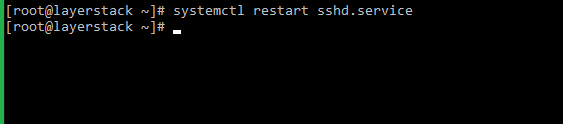
# systemctl restart sshd.service (CentOS/Fedora)
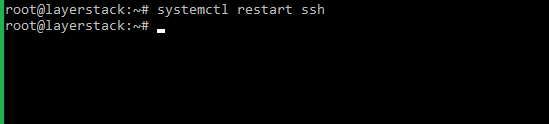
# systemctl restart ssh (Ubuntu/Debian)
1. Set up SSH Key-based authentication
Although SSH server different methods of authentication, the recommended authentication method, when it comes to security, is the public key-based authentication. The below guide can be referred to set up SSH Key-based authentication for all Linux OS.
https://www.layerstack.com/resources/tutorials/How-to-set-up-SSH-keys
2. Disable SSH root user login
Another method of securing the SSH server is to disable SSH login for the default root user. It is required that another user created in the server is permitted to log in as root, before disabling root login. In the context of this article, the user account being used is layerstack.
The below commands can be executed in order to grant root privileges to a user account.
# sudo usermod -aG wheel layerstack (CentOS/Fedora)
# sudo adduser layerstack sudo (Ubuntu/Debian)
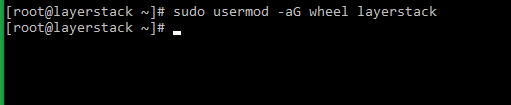
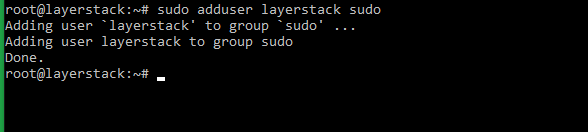
Once sudo access is verified, SSH root login can be disabled by setting the below values in the SSHD configuration file.
PermitRootLogin no ChallengeResponseAuthentication no PasswordAuthentication no UsePAM no
NOTE: All the above variables are present in the SSHD configuration file by default, only the values need to be adjusted.
3. Disable password-based login
For security purposes, all password-based logins should be disabled and only public key-based logins should be allowed. For enabling public key-based logins, the below values need to be set in the SSHD configuration file.
AuthenticationMethods publickey
PubkeyAuthentication yes
For older versions of the SSH server (on older versions of CentOS), only the below setting is required.
PubkeyAuthentication yes
4. Limit SSH access for user accounts
By default, all user accounts created in a Linux server can log in to SSH using their respective passwords. These user accounts can include users created for the purpose of other services such as email, FTP, etc. They can log in to SSH and have access to system tools that can be used for unfair practices and this can severely compromise the security of the server itself.
SSH access can be allowed for certain user accounts as well as denied for specific user accounts by making use of the below variables that can be added to the SSHD configuration file.
For allowing SSH access, add the below line in the SSHD configuration file:
# AllowUsers layerstack1 layerstack2
This allows root (by default) and the user accounts layerstack1 and layerstack2 to use the server through SSH.
For denying SSH access, add the below line in the SSHD configuration file:
# DenyUsers root layerstack2
This allows SSH access to the server for all users except the root user and the user account layerstack2.
5. Disable Empty Passwords
Remote SSH login from a user account with empty passwords should be compulsorily disabled in the server. For this, the below setting needs to be updated in the SSHD configuration file.
PermitEmptyPasswords no
6. Use strong and complex SSH passwords and passphrase for SSH key-based authentication
Weak passwords are one of the main reasons that compromise SSH security. It is always recommended that a strong and complex password/passphrase be used for SSH root users as well as for SSH key-based authentication.
A strong password should follow the below criteria:
i) It should have a minimum length of 8.
ii) It should be a combination of uppercase and lowercase alphabets, numbers and special characters.
iii) It should contain at least one uppercase alphabet, one lowercase alphabet, one numeral and one special character.
iv) Never reuse old passwords.
7. Restrict SSH access to specific IP addresses
Setting up IP-based restrictions for SSH access is a suggested method to secure the SSH service of a Linux system. Rules can be set up using the firewall application of the server for restricting SSH access to specific IP addresses.
Below are some examples of firewall rules that allow SSH access on port 22 for IP address 1.2.3.4 only.
Using iptables:
# sudo iptables -A INPUT -s 1.2.3.4/24 -m state --state NEW -p tcp --dport 22 -j ACCEPT
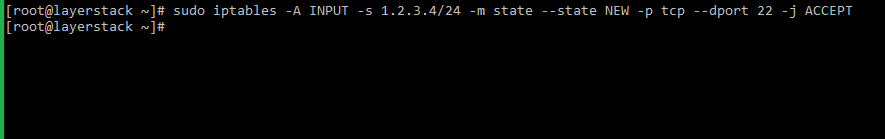
Related article: https://www.layerstack.com/resources/tutorials/firewall-configuration-using-iptables-on-ubuntu-14-04
Using firewalld (CentOS7/8):
# firewall-cmd --zone=internal --add-service=ssh --permanent
# firewall-cmd --zone=internal --add-source=1.2.3.4/32 --permanent
# firewall-cmd --zone=public --remove-service=ssh --permanent
# firewall-cmd --reload
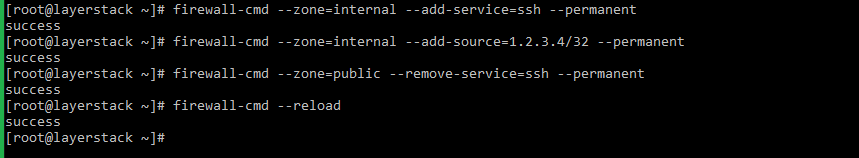
Related article: https://www.layerstack.com/resources/tutorials/How-to-set-up-and-configure-firewall-using-FirewallD-for-CentOS8
Using UFW (Ubuntu/Debian):
# sudo ufw allow from 1.2.3.4 to any port 22
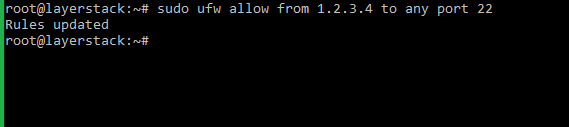
Related article: https://www.layerstack.com/resources/tutorials/How-to-set-up-configure-Ubuntu-Firewall-for-Ubuntu18
8. Change SSH port and limit IP binding
Changing the SSH default port (22) to any other random port is always the best option to secure the SSH server since most of the brute-force attacks to a server are directed towards the default port.
The below article explains the steps involved in changing the SSH port for the server.
https://www.layerstack.com/resources/tutorials/How-to-change-SSH-port-on-Linux-Cloud-Servers
In the case of servers having multiple IP addresses, SSH service can be limited to listening to specific IP addresses in the server using the ListenAddress directive. This should be added to the SSHD configuration file in the below format, where 1.2.3.4 is the IP address to which the SSH service needs to listen.
# ListenAddress 1.2.3.4
9. Configure idle log out timeout interval
Unattended SSH login sessions can be controlled and terminated by setting up an idle-timeout interval value in the SSHD configuration file. The below setting needs to be updated for this purpose.
ClientAliveInterval 300
ClientAliveCountMax 0
The above setting simply denotes that a user account will automatically be logged out of the server once after 5minutes (300 seconds) of idle session time.
10. Setup a warning banner for SSH users
A warning banner can be set for a server by adding the below entry in the SSHD configuration file.
# Banner /etc/issue
The /etc/issue file can then be updated with a relevant service user agreement and legal notice details as required by the server owner.
11. Disable host-based authentication
Host-based authentication allows hosts to authenticate on behalf of all or some of the users of that particular host. For SSH security, this directive should be disabled in the SSHD configuration file.
Update the configuration file with the below entry for this:
# HostbasedAuthentication no
12. Always keep the SSH server and operating systems updated
A major consideration when it comes to the security of SSH service, as well as any other service in the server, would be to keep the operating system as well as the relevant service updated and patched.
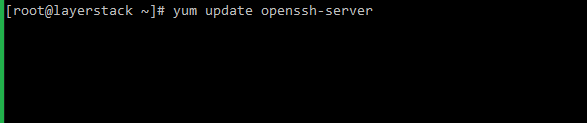
Package installer tools such as YUM, apt-get, etc can be used to update the SSH service with the latest security patches.
# yum update openssh-server (CentOS/Fedora)
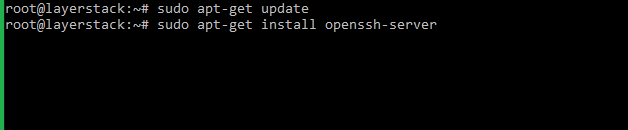
# sudo apt-get update (Ubuntu/Debian)
# sudo apt-get install openssh-server (Ubuntu/Debian)